Hello everyone,
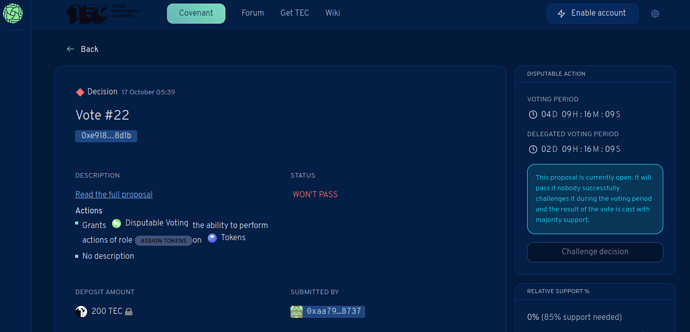
The address of a community member has been compromised, and he asked me to prepare a vote to revoke their TEC vesting and assign it to another address. To do so, the whole community has to vote through a Tao Voting in the garden here.
The vote will grant permission to revoke vestings to Tao Voting and then use Tao Voting to revoke the vesting for 0x5c44E8982fa3C3239C6E3C5be2cc6663c7C9387E, returning the locked tokens to the token manager address. In a subsequent vote, we can assign those tokens again to a new address provided by this member, respecting the vesting schedule of the rest of the hatchers.
I know that Tao votes should take more time and go through the advice process, but it looked to me that the sooner this vote passes, the fewer TEC tokens the attacker will have. Of course, if somebody thinks it is not enough justified reason, they can challenge the proposal, and I will gladly retire it and go through the standard procedure. Still, I think it should be fine to make an exception in a case where there is a compromised address and funds at risk.
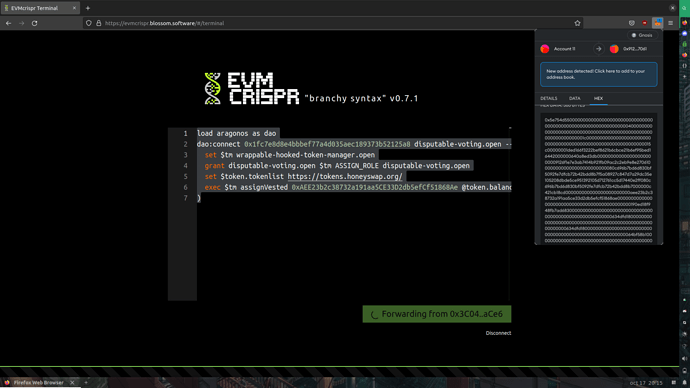
EVMcrispr script used
load aragonos as dao
dao:connect 0x1fc7e8d8e4bbbef77a4d035aec189373b52125a8 disputable-voting.open --context "Revoke hacked account vesting" (
grant disputable-voting.open wrappable-hooked-token-manager.open REVOKE_VESTINGS_ROLE disputable-voting.open
exec wrappable-hooked-token-manager.open revokeVesting 0x5c44E8982fa3C3239C6E3C5be2cc6663c7C9387E 0
)